Save time and money with Monitask time tracking software. Need to track employee time?
Time is one of the most valuable assets today, especially for busy professionals. That’s why it’s so important to be able to track and manage your time efficiently. Monitask is an all-in-one employee monitoring tool and time tracking solution.
This tool is designed to help employers and project managers to make the most of their agenda by providing a comprehensive time tracking software and project management tool that fits each workflow.
Monitask can easily track employee hours, monitor team productivity tracking, create invoices, generate detailed reports, and project planning with advanced, reporting features such as task dependencies and automated notifications.
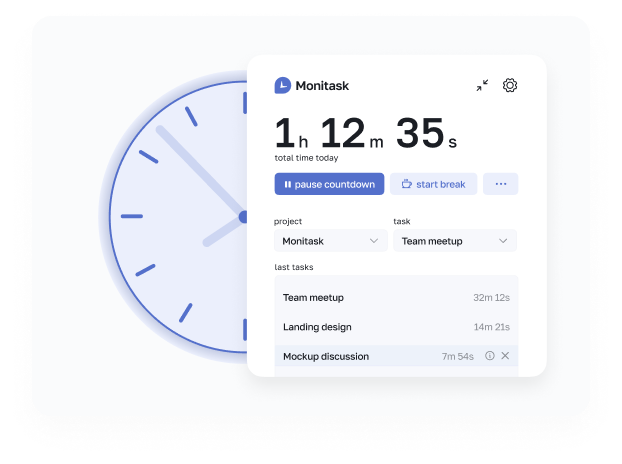
With our software, you can also set up automated time tracking to keep an eye on team activities during work hours, even when you’re away.
Monitask not only has the most basic time tracking features but also works as a project management software. Start your 10-day free trial here!
The history of time tracking goes back to ancient timekeeping cultures. Ancient Egyptians started time tracking using the sun as a guide, and later, the Greeks used sundials to measure time. With the invention of clocks, time tracking became more precise and accurate. As computers became more widespread, electronic time tracking software became more accessible.
By the 2000s, web-based and mobile time tracker systems were developed, allowing employers and employees to track time remotely. Using a time tracker app is more secure, easier to use, and offers many additional features like GPS tracking, automated invoicing, task management, and timesheet reports.
From paper timesheets to a desktop app, the concept of time or timekeeping has undergone constant evolution to get where we are now: employees can digitally keep track of their work hours with minimal effort.
Before the advent of software-based time tracking software, punch cards were used to record employee work hours. This system required employees to punch in their ID cards at the start and end of their shifts and was a popular method for decades.
Punch cards can be easily imprinted by others, but if someone happens to forget their punch card, then that person’s hours remain unaccounted for. This could leave employers with incorrect data to make decisions about payroll or workforce allocation.
Paper timesheets have been the primary way of tracking time for many years in businesses. Employees would fill out their working hours, manually, on a paper timesheet and submit them to their supervisors or managers for review.
Considering this method was labor-intensive, prone to errors, and difficult to track when multiple workers were involved, paper timesheets were incredibly inefficient and often inaccurate due to manual errors.
Nowadays, with the advent of digital time tracking software, it is much easier to measure employee work hours with more accuracy and efficiency than other tools. Employers can now track their employees’ attendance and performance, and create projects using advanced time tracking tools.
By implementing technological solutions employers can store the relevant data in one secure platform, keep updated information on the working times of their staff, and perform accurate time entry.

This technology enables automatic time tracking of the entire clock-in/clock-out process and makes it easy to track working hours accurately, minimize payroll costs, budget forecasting, monitor team productivity, and more.
The best time tracker app offers a modern and efficient way to track your hours worked and activity logs in one central digital hub. A time tracking app is incredibly useful for entrepreneurs, freelancers, and employees alike for a variety of reasons.
One of the great things about tracking app is how they enable employees to record their time accurately and conveniently from any location – including remotely – on laptops or mobile apps, which is a great advantage in today’s increasingly remote work environment.

Monitask understood the transformation of time tracking tools over time, and integrated project management features with employee monitoring into an all-in-one software with an intuitive interface to be used by unlimited users at a better price than other time tracking software.
Monitask is now one of the best time tracking software in the market designed to fit any industry!
Read our blog on “How to Make Sure You’re Not Being Cheated by Freelancers: Definitive Guide To Billable Hours (And How To Record Them)” here.
Most staff monitoring software is installed on employer-owned devices, such as laptops or smartphones. However, some software can also be installed on personal devices, if employees are using these devices for work purposes.
Once installed, the software will run in the background, tracking employee activity and generating reports. These reports can be accessed by employers at any time, giving them a detailed overview of their team’s activity.
Staff monitoring software can track a variety of employee activities, including:
Some of the best time tracking software also includes features such as GPS tracking or geofencing, which can be used to track employee location. This data can be used to see if employees are working from home or taking unauthorized breaks.
Choosing the right time tracker for your business can be a challenge. There are many different options on the market, and each one offers its own unique set of features.
As a business owner, implementing the best time tracking tools into your business processes can be an effective way to track time and attendance tracking of your team or remote workers.
Using a time tracking tool can give you greater insight into how your company runs, what processes need improvement, and the time spent on each task.

Most employee monitoring software is flexible and customizable enough to suit any industry for unlimited users, meaning it can quickly become an invaluable tool for productivity analysis and accuracy in the workplace.
Our software serves as an all-in-one hub for your business, providing project management features and employee monitoring capabilities.
With its intuitive interface, Monitask is perfect for:
Employee time tracking apps can be a useful tool for managing your projects efficiently and mitigating employee burnout.
It enables managers to monitor employee productivity and workload distribution amidst multiple tasks and departments, ensuring that all employees are working their best towards their goals.
Monitask helps you plan, organize, identify and prioritize your unlimited projects, also allowing real-time collaboration and communication with team members to keep everybody in the loop.
Monitask’s user-friendly interface offers an intuitive experience of project management tools for both experienced managers and beginners alike, making it easy to create schedules and check on changes quickly.
Monitask is the perfect choice for anyone who wants to implement popular project management tools with time tracking solutions.
If you are a project manager, struggling to make everything work, or simply wanting to innovate your workflow, read our blog: “15 Must-Read Project Management Blogs: The Top Resources for Every PM” here.
Maintaining productivity and trust with remote employees can be a challenge. Time tracking apps are a great tool for monitoring remote employee hours, ensuring that everyone is putting in the necessary work hours.
Monitask is the ideal employee time tracking software that fits the modern workplace, providing additional features such as up to three screenshots in mere minutes, with no keystroke monitoring, website, and employee activity tracking, to ensure that remote employees are staying on task during their working hours.
Monitask also offers integration with popular work management systems, like Asana or Trello, making it simple to customize your remote monitoring solution. Our software is secure and easy to use, providing an innovative and efficient way for businesses to stay on top of their remote employees in real time.
Productivity is one of the best assets a company has, however, social media usage by the average worker during work time can hinder overall company performance.
Approximately 9.4% of people spend more than two hours per workday scrolling through social media, translating to about 40 hours a month that is wasted away on this activity alone.
Monitask is a synonym for high productivity. Our intelligent time tracking feature packed with powerful analytics will track time spent on different activities and tasks. Monitor time spent across different projects to keep an eye on deadlines and time limits for certain activities, optimizing the whole team’s time.

Habitual internet and application usage can cause major dips in productivity. Monitask allows employers to monitor which activities are taking up most of their employee’s time, so they can take steps to improve performance.
According to Zippia, employees can spend up to 32% of their time on Facebook, costing employers $28 billion each year. Monitask tracks both applications and websites used by employees across all devices, allowing you to stay on top of employees’ online activity and ensure they’re working efficiently.
Activities like social media, streaming, and gaming can be monitored with Monitask’s advanced filtering capabilities. Hopping on Monitask is easy. Just sign up with your email address and get started tracking time and managing projects today!
Monitask simplifies the time-consuming process of creating invoices, allowing you to generate professional invoices efficiently and accurately. Monitask also functions as an expense tracking software as it provides real-time data on the time entries and activities associated with each task.
When combined with the notification capabilities, makes it easy to produce accurate invoices that will help maintain relationships with clients or contractors.
Monitask is a breakthrough in time tracking, offering easy and efficient solutions to various industries. Many industries have adopted Monitask in need of accurate tracking solutions such as software developers, marketing teams, creative professionals, lawyers, contractors, freelancers, human resources specialists, and more.
Monitask allows teams to track billable hours, planned projects and tasks, activity times, and expenses quickly and easily. This innovative platform also enables organizations to monitor employee performance, allowing them to identify areas of improvement for greater productivity and efficiency.
Monitask tracking app has revolutionized the way individuals and companies manage their time tracking processes, providing a convenient and cost-effective solution.
Monitask helps consultants bring a professional touch to their work. As consultants provide valuable services and advice, Monitask provides them with an accurate and active way to record their progress.
Monitask enables consultants to better manage their tasks and associated timelines, so they can efficiently invoice for their services and receive payment quicker for their accomplishments.
Monitask is positioned as a useful tool for consultants around the world, helping them save time and money while managing themselves effectively – allowing them to continue providing high-value advice.
Freelancing brings with it a variety of rewards such as flexibility, the ability to work with multiple clients at once, and increased self-esteem.
Monitask provides freelance professionals with exactly what they need: an improved and streamlined approach to wage transparency, accurate tracking of projects, and continuous access to project milestones.
Read our “Expert Guide to Keeping in Touch With Remote Employees and Hourly Contractors” here.
Monitask empowers freelancers to optimally use their time while at the same time eliminating any room for discrepancies or misunderstandings over wages. Monitask is the perfect choice when it comes to efficient time tracking that makes a big difference in freelancers’ earning potential.
As a small business, there are many challenges that you face every day; however, having the right tools can make all the difference. Time tracking software can help tremendously with managing tasks, tracking productivity, and monitoring hours accurately.
By understanding how your team is spending their time, you can optimize their efficiency to maximize results without sacrificing quality. It can also provide visibility into different parts of your business processes and identify ways to streamline operations and cut costs effectively.
Monitask desktop app is the go-to choice for small businesses that want to maximize their time tracking so they can focus on what matters most – growing their businesses.
Using a time tracking software only for you can be a great asset when it comes to managing time and staying organized. Not only is having an individual account with a time tracking software convenient and easy but it can also help the user gain insight into how they are using their time each day.
Time tracking software allows users to observe patterns in their daily tasks, enabling them to adjust and most effectively use their time.
Time tracking software can also serve as a way of motivating and organizing users by providing reminders and by helping them stay on top of appointments and deadlines.
Time tracking software for accounting firms is an invaluable tool. It allows a firm to quantify the number of hours worked on each project and accurately calculate accurate billing totals. Time tracking also assists with employee productivity management and compliance, ensuring staff follows procedures and reporting requirements appropriately.
Time tracking systems make payment easy for clients, and can help a firm maximize its profitability by allowing its staff to work smarter and more efficiently. Time tracking software for accounting firms provides an efficient, cost-effective way to better manage projects, track time and expense expenses, speed up billing cycles, improve customer service and increase profitability.
Contractors must ensure that their time billings are accurate to comply with any local or federal permits and accounting regulations. Time tracking software for contractors can help manage the many tasks associated with their profession like consulting and ensuring payment for hours worked.
Using the right application can make a huge difference in managing projects. Monitask is an all-in-one time tracker and employee monitoring tool designed for professionals including contractors. It is important to select the correct tool when choosing a time tracking software program that best serves their needs.
Time tracking software for lawyers is a valuable tool that can help manage legal practices. This type of software provides firms with an easy-to-use system to track the amount of time that employees spend on various tasks such as preparing for court cases or researching potential clients.
Time tracking software for lawyers can save firms time and money, as well as provide insights into employee productivity and satisfaction.
By monitoring work hours and activities, lawyers have more control over their client’s outcomes, leading to improved customer experiences and better results in court cases.
Time tracking software for virtual assistants is an invaluable tool that allows virtual assistants to carefully monitor their work time and ensure they are being properly compensated.
Not only can this software accurately record the amount of work being completed, but it can also provide potential employers with details on what tasks have been completed and how long each task took to finish.
Time tracking software for virtual assistants puts all of the pertinent information within one convenient location, which allows users to make well-informed decisions about when, how, and why tasks should be completed. Anyone interested in working as a VA should invest in time tracking software like Monitask.
Time tracking software for designers is becoming an increasingly popular tool among creative individuals in the industry. It helps streamline design processes by providing users with real-time insights into how long tasks are taking to complete.
Time tracking platforms also offer customizable reports, allowing designers to gain greater clarity on where their time is going so that they can make better decisions about how to plan projects in the future. Time tracking software for designers helps to budget tracking so that the best possible results can be achieved.
Monitask is a cloud-based software platform that is available for different operating systems including macOS, Windows, iOS, and Android, as well as web applications. This gives managers and administrators an incredibly wide range of options when it comes time to supervise and report on employees and unlimited users without restricting them just to one operating system.
This tool is quickly becoming a necessity for companies of all sizes. By tracking work time on the go, enabling GPS tracking, and having it be compatible with Apple mobile phones, businesses can save valuable resources that can be invested elsewhere.
Not only does time tracking software for iPhone allow businesses to monitor their workforce in real-time, but its cloud storage capabilities also ensure that all data is securely stored off-site, giving businesses peace of mind and an efficient way of running their operations remotely.
Monitask is the best time tracking tool for macOS providing a convenient application for Apple laptop and desktop users to stay organized and to have better control of their time. With Monitask, Mac users can easily monitor time entries of their activities to maximize productivity.
Monitask time tracking software for macOS is highly accessible. With its cloud-based storage, documents can be retrieved whether you’re on the go or at home, whether you need help with organizing your life or a business wanting better management of resources.
Monitask time tracking software for Windows enables employers to accurately track employees’ clock-in/out times, hours on the job, day offs, and PTO. By using this data employers can create detailed attendance reports ensuring accurate payroll calculation and cost savings from increased efficiency.
Furthermore, time tracking software compatible with Windows provides users with an easy-to-use interface, helping teams of all sizes manage their time and resources more effectively.
Time tracking software for Windows proves essential in improving workflow management and reducing potential risks arising from incorrect logging or manual entry errors.
Monitask is an intuitive tool like any other time tracking software for Linux, tested and verified on the Ubuntu 16.04-18.04 and Debian 9.9 variants of the Linux operating system as well as Mint 19.1.
The .deb package can be downloaded on most Debian/Ubuntu distributions, which installs its related apt repository for easy auto-updating with your system’s package manager.
Similarly, Monitask’s .rpm package has been tested compatible with Fedora 28-30, CentOS 7, and Red Hat Enterprise Linux 7, enabling users to also easily update their time tracking software using their system’s package manager.
iOS, macOS, Windows, and Linux devices are all supported by Monitask!
Monitask time tracking software is the perfect solution for businesses looking not only to use it as a time tracker but also to manage tasks and performed project planning.
Choose Monitask time tracking software for business if you want:
Monitask’s innovative time tracking software is the ideal solution for businesses that want to improve the engagement of their employees. This powerful tool measures the effectiveness of different strategies so that managers can be better equipped to develop techniques for getting staff more committed and motivated. Knowing their productivity is being closely monitored.
Monitask also encourages team members to become more accountable for their work, as well as increasing their level of engagement with each task or project. Monitask’s time tracking software is a must-have for any business looking to improve employee engagement.
Like no other tool, Monitask is the best time tracking software to help businesses effectively manage time to reach their goals. With the Monitask time tracking app, businesses can easily evaluate project progress and work completed to understand the time it takes to complete particular tasks. This helps managers identify and resolve any time-related issues before they become a problem.
Monitask tracking app offers a streamlined way to project management and upcoming tasks or deadlines. With an easy-to-use interface, Monitask is perfect for businesses that want improved transparency on their project status. Monitask offers detailed reports on all current projects to stay informed and plan out tasks efficiently.
This allows tracking of team performance as well as the overall progress on all projects, ensuring that everything runs smoothly and deadlines are met with confidence.
Monitask is the time tracking software that helps any business with increased visibility and clarity into what stage each project is at.
Monitask is one of the best programs for businesses looking to take advantage of integrations. This time tracking tool allows users to sync tasks and projects with popular business applications such as Asana, Zapier, and Trello.
If you use other integrations, read our blog on “10 Must-Have Project Management Tools to Integrate with Monitask” here.
Monitask makes it easy for users to integrate their Monitask account with these other systems so that they can quickly manage both tasks and timesheets in one place. Monitask provides businesses with powerful tools to help them achieve success in all areas of the organization!
Monitask provides unsurpassed accuracy in time tracking activities and makes it easy for you to keep track of billable hours worked, ensuring that you’re not wasting valuable resources. With Monitask’s comprehensive reporting capabilities, organizations can quickly drill down into the details of employee performance, enabling them to make decisions based on real-time data and save money.
Monitask’s automated time tracking system shows how much time was spent on each project or task, allowing businesses to budget accordingly by easily determining which projects were billed in line with the expected billable hours.
Monitask is the ultimate solution when it comes to managing accurate cost calculations based on precise billable hours information.
Monitask offers an industry-leading combination of automated functionality and one-click access to a host of reliable data storage solutions. These solutions include secure cloud hosting, 2FA authentication, and encryption, ensuring all your data remains private and confidential at all times.
Monitask also provides excellent customer support options such as automatic backups and cloud storage so security can always be ensured. With Monitask, you can access the latest features and ensure that your data is well protected against any potential threats.
Monitoring employees raises several privacy concerns. For example, employees may feel like they are being constantly watched and monitored, which can lead to feelings of anxiety and stress. In addition, employees may feel like their employer is not trusting and this can damage the employer-employee relationship.
While selecting this type of tool for your organization, it is important to:
Monitask ensures that its time tracking system is easy, fast, and simply operated so employees can record their attendance or work hours quickly and without challenges.
There are many different time tracking software available, so make sure to choose one that fits your needs. Yet, if you’re not sure where to start, we’ve got you covered with our list of the best time tracker with project management capabilities!
Monitask is an all-in-one staff monitoring solution that offers a wide range of features, including screenshots, activity tracking, and productivity reports. Monitask also includes a desktop app and a mobile app, so you can monitor employee activity from anywhere.
One of the great things about Monitask is that employees, field contractors, and independent contractors can manually clock in when they start working on a project, in this way you can monitor your employees because the application will randomly or routinely take screenshots.
By using Monitask you get access to:
Monitask is quickly gaining traction among companies, teams, and remote workers who aim to improve their timekeeping and efficient project management.
TimeDoctor is a popular staff monitoring solution that helps businesses improve productivity and efficiency. The software records employee activity, including computer usage, internet browsing, and email usage.
It also tracks employee idle time and provides detailed reports on employee productivity. Time Doctor helps businesses to identify employee productivity issues and provides recommendations on how to improve employee productivity.

Hubstaff is software to monitor employees with the feature to take screenshots and monitor activity levels. This tool generates time tracking reports and helps to manage your workforce by monitoring payroll, scheduling, and invoice tracking.
It also allows employers to see which apps and websites are being accessed to identify potential productivity problems.
Hubstaff also offers a variety of features designed to always keep an eye on your employees while they are on the field with GPS location tracking and geofence time tracking.
Toggl is a comprehensive time tracking software designed to help businesses maximize productivity and efficiency. Toggl provides features like in-depth analytics, real-time reports, and automated reminders apps for tracking time where it matters most.
Toggl Track users can also access shared team dashboards for collaboration and visibility into workloads. Toggl’s timesheets enable effortless payroll processing and confidently knowing how tasks are distributed among teams. Toggl also gives the user access to invoicing features so they can bill clients through their platform with ease.
Harvest offers business owners powerful time and billing management software to help them stay organized and on top of their expenses.
Harvest makes it easy for small businesses and freelancers to compete with the big players in their field by streamlining their administrative processes and increasing visibility over their finances.

Harvest doesn’t offer the robust task management features that other service tracking programs, such as Monitask, do. With its advanced task assignment, time tracking, reporting, and invoicing capabilities, Monitask is an excellent choice for those who need reliable tools to manage projects swiftly and efficiently.
DeskTime is desktop monitoring software that allows employers to track employee activity. It takes periodic screenshots of the desktops of all employees and records which applications and websites are being accessed.
This information is then aggregated and presented in a report, which can be used to assess productivity levels. DeskTime can also monitor idle time, invoicing, cost calculation, and absence calendar, with an integrated Pomodoro timer.
ActivTrak is a great way to keep track of your employees and their work habits. With ActivTrak, you can take screenshots of your employees’ workstations, so you can see what they’re doing and how they’re doing it.
ActivTrak also allows you to monitor employee activity, so you can see what they’re working on and how much time they’re spending on it. In addition, you can review employee engagement, productivity monitoring, SaaS management, employee burnout, and much more.
RescueTime offers tools for productivity and time management, helping to keep users focused and productive by knowing exactly how much time tasks take to be completed. RescueTime provides a detailed analysis of your online activities, tracking website visits, app usage records, and more.
Using this data, RescueTime generates productivity scores and reports to provide insightful recommendations for improved time management.
Compared to RescueTime, Monitask goes one step further in promoting increased productivity by offering an array of features geared toward task management and collaboration.
Although RescueTime is capable of tracking productivity metrics on the individual level, Monitask is superior when it comes to collaborative projects with employees or team members.
TimeCamp is a comprehensive software that can help businesses stay organized and maximize their productivity. This tool provides cloud-based software solutions, including time tracking, project management, budget tracking, and more.
TimeCamp’s intuitive user interface makes it easy to set up projects and establish deadlines so teams always have clear guidance on their tasks.
With TimeCamp, employees have the freedom to track their time, as well as assign tasks, and monitor progress remotely with its integrated mobile app.
TimeCamp’s analytics suite also allows users to get away from the guesswork when analyzing data – they can easily view trends in a team performance that can be used to create better strategies for employee engagement.
Monday.com is an invaluable asset for businesses looking to collaborate more efficiently and make informed decisions. Monday’s intuitive platform makes it easy to visualize complex work plans, monitor progress, receive updates on tasks, and even manage budgets through customizable dashboards.
Unique features such as assignable states and timeline views offer unparalleled visibility into any project, enabling teams to quickly spot inefficiencies and take corrective action before deadlines are missed.
Monday’s combination of practical tools, flexibility, and reliability makes it a great organizational solution for any organization.
Monitask is more than a simple time tracking app, it’s an all-in-one hub for time tracking app, project management, and employee time tracking software, along with reporting features and productivity analysis!

What can Monitask do for you?
With its easy-to-use timesheets and flexible tracking options, Monitask makes it simple to stay on top of your work hours and billable tasks.
Whether you’re tracking employee timesheets or managing your own time, Monitask makes it easy to see how much you’ve worked and what projects are taking up the most of your valuable time.
Monitask is a simple and effective way to track productivity and focus. By monitoring which tasks are being completed, and how long they take, our software can help to identify areas of improvement.
By using Monitask, individuals can increase their productivity, and get a better understanding of where their time is best spent.
If you bill your clients by the hour, it’s important to track work hours your employees spend working on each project. With our web-based time tracking solution, you can easily generate invoices based on the hours worked, so you can get paid for the work you do.
Whether you are a small startup or an established business, we can create a customized employee scheduling solution that meets your unique needs.
Our solutions combine industry-leading software tools with unparalleled expertise in human resources to deliver highly efficient services that give you greater control over your team’s assignments, workloads, and days off. If you are looking for a reliable and cost-effective unlimited tracking solution for your business, invest in Monitask as the best time tracking software today!
Step 2
Click "Invite your team" from the dashboard and add your team members’ email addresses. You can add an unlimited number of employees to your account.
Step 3
Your team members will need to download the time-tracking app and start using it to track the time spent on work items. Company owners, administrators, and managers do not need to install Monitask, as data is accessible via the web-based real-time dashboard.
Step 4
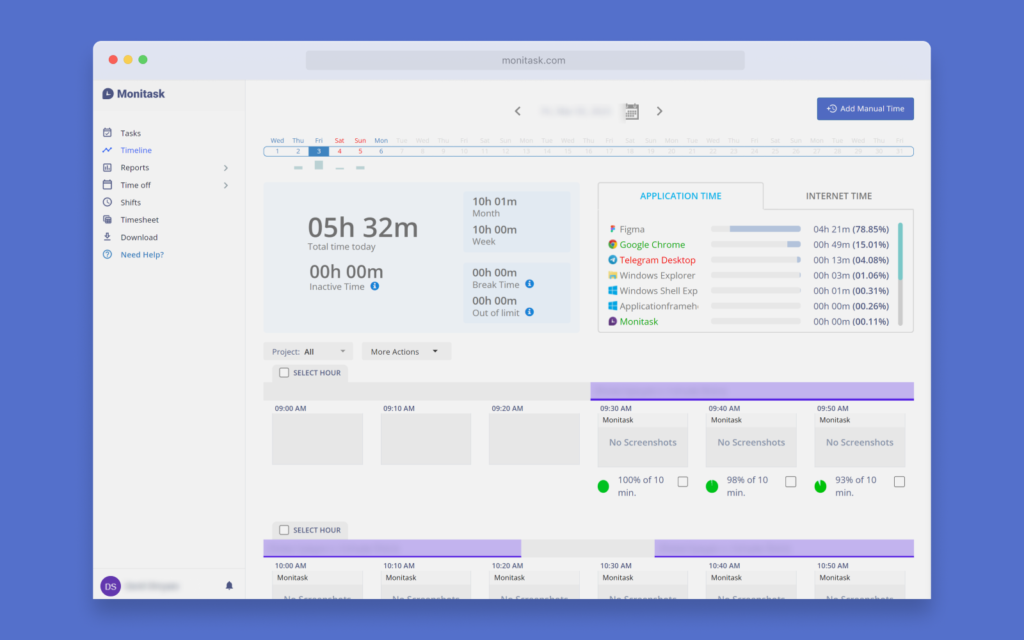
Use Live Dashboard to review online employees, their time entries, screenshots, activity levels, and internet usage.